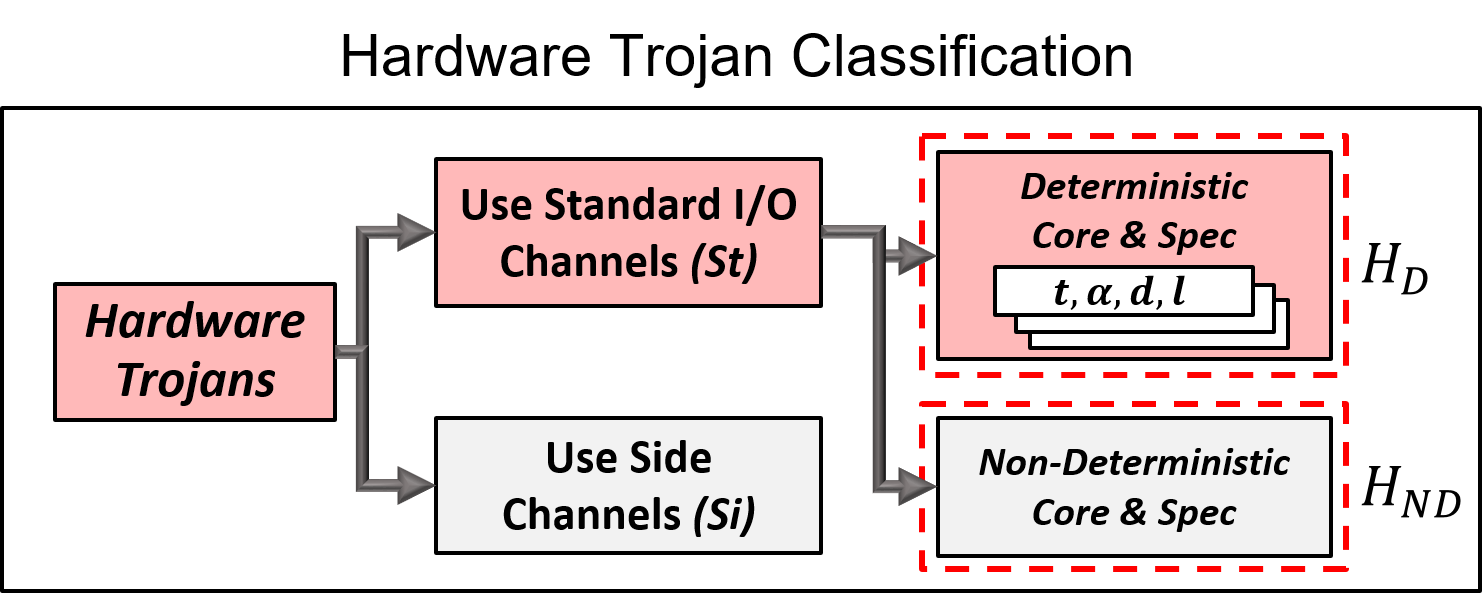
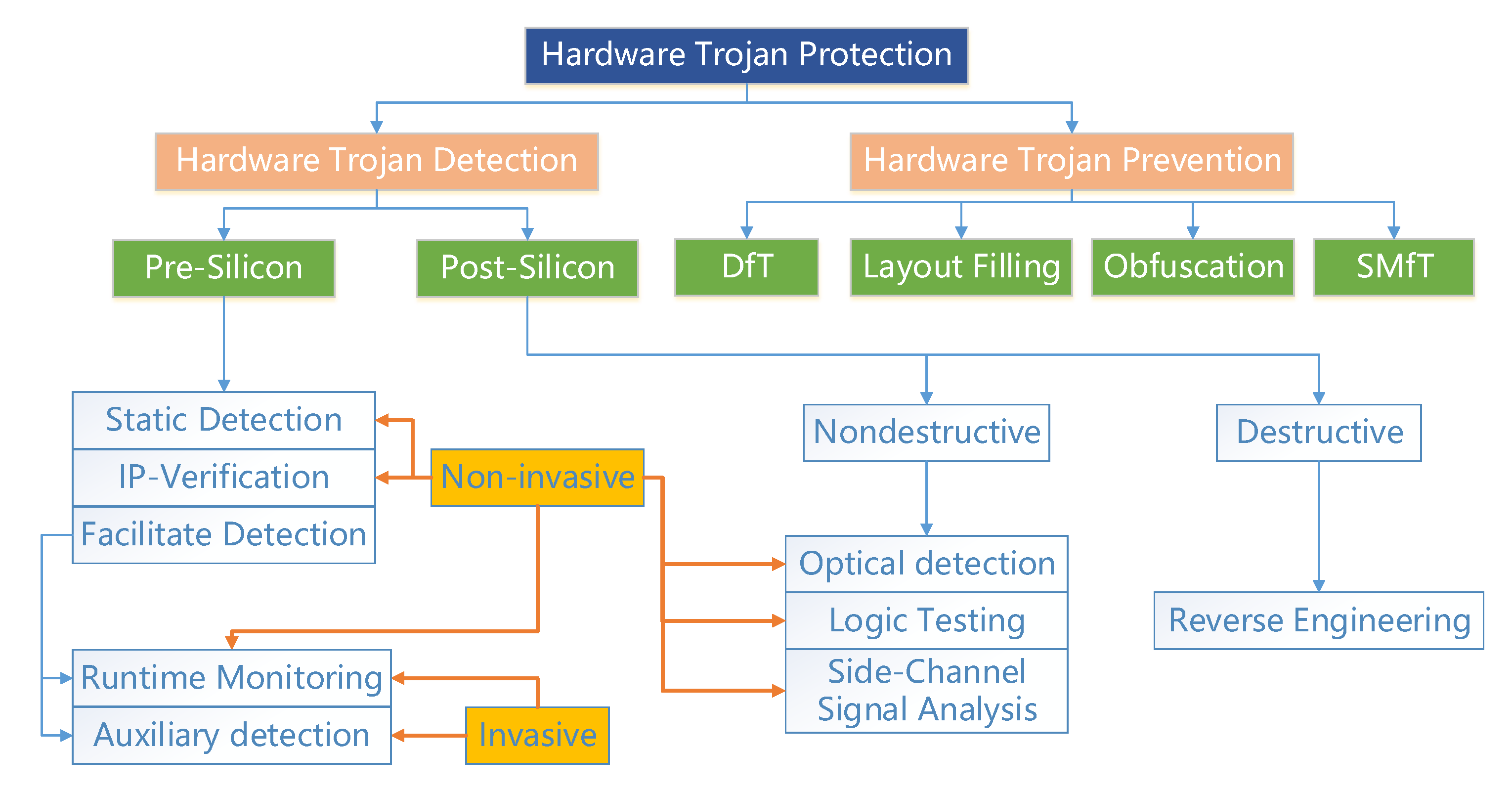
Improved Test Pattern Generation for Hardware Trojan Detection using Genetic Algorithm and Boolean Satisfiability

Detecting Hardware Trojans Inserted by Untrusted Foundry Using Physical Inspection and Advanced Image Processing | SpringerLink

A machine-learning-based hardware-Trojan detection approach for chips in the Internet of Things - Chen Dong, Jinghui Chen, Wenzhong Guo, Jian Zou, 2019

UNREVEALED FILES ™ on Twitter: "Hardware Trojans are becoming increasingly common and concerning in recent years due to growing numbers of attacks such as data theft and backdoor insertions into the electronics

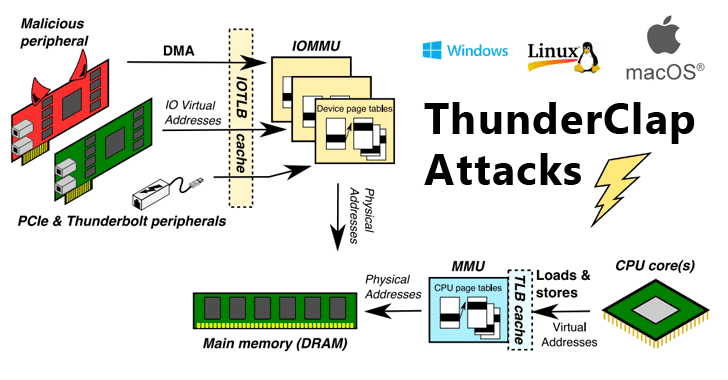







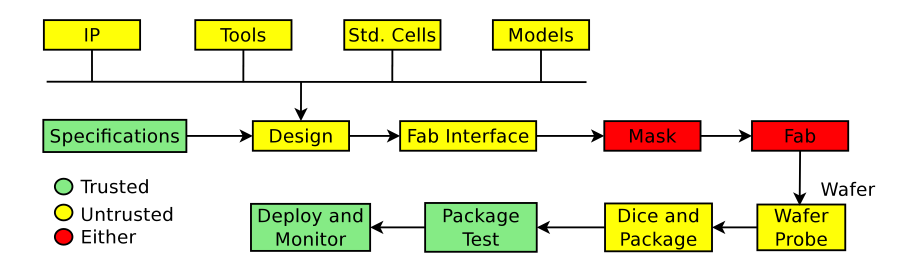




![PDF] Trustworthy Hardware: Identifying and Classifying Hardware Trojans | Semantic Scholar PDF] Trustworthy Hardware: Identifying and Classifying Hardware Trojans | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/4d9d3df6f23afef5605ae45b46deb30ffe13894f/3-Figure1-1.png)